Using the Netstat Command to Monitor Network Traffic
- Blog
- Networking
- Post
There are a number of different tools that are available to help in the configuration and troubleshooting of networks. Many of these are included as part of the operating system, which makes them even more useful because they are included on most computers automatically. This article takes a look at the Windows implementation of the netstat command, although there are versions of netstat available for many other OSes.
What Is the Netstat Command?
Well if we are to use the most obvious description, the netstat command (short for “network statistics”) is used to display protocol statistics and current TCP/IP network connections. While this may sound simple, it can be used to find a large amount of information about the state of the connection into the device including, but not limited to: which ports are open for incoming connections, which ports are actively in use, the current state of existing connections, in-depth protocol statistics, and many other useful pieces of information.
How Is the Netstat Command Used?
To ensure the best understanding of how the command is used and what information is returned, the easiest way for me to show you how to use netstat is to use several examples of useful output. This section takes a look at some of the most common command options and what output can be expected from their use.
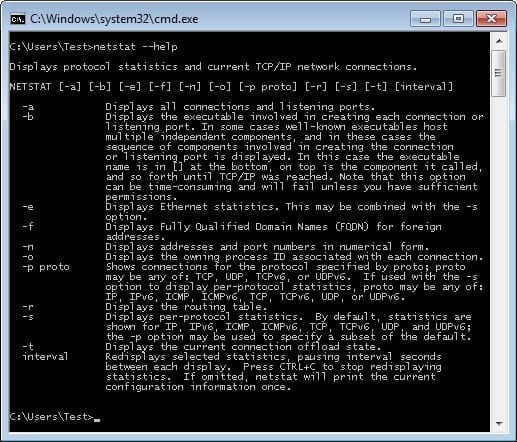
Below, figure 1 displays the options that are available for use with the netstat command — without any additional parameters the command will return a list of the active connections on the device.
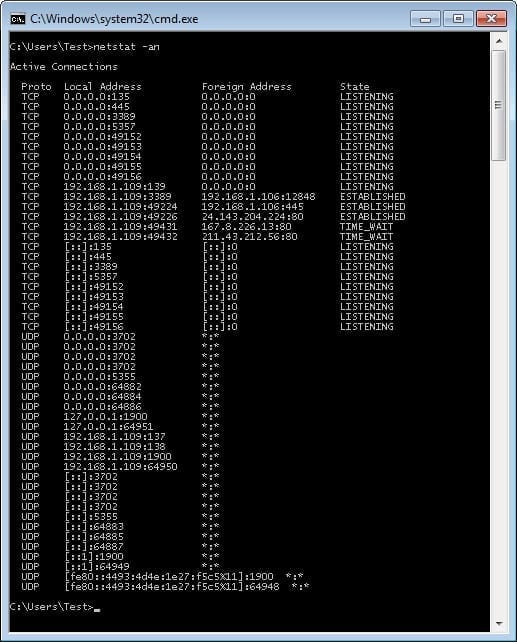
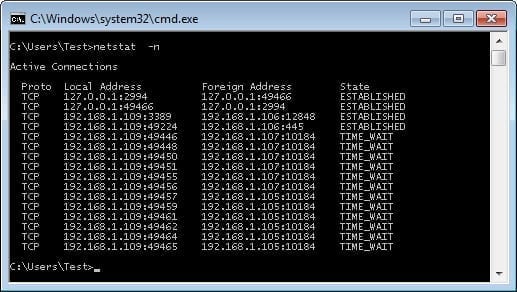
A version command parameter combination is to use the -a and -n together, this will display all of the connections (active and listening) as well as disable the use of DNS lookup. The question might be why would be it important to disable DNS lookups. This is typically used for two reasons: DNS lookup takes time, and it’s often not necessary to perform the lookup for the information being sought. Also, it’s usually best when troubleshooting to look at things without the extra layer of naming. An example of these two options being used together is shown in Figure 2.
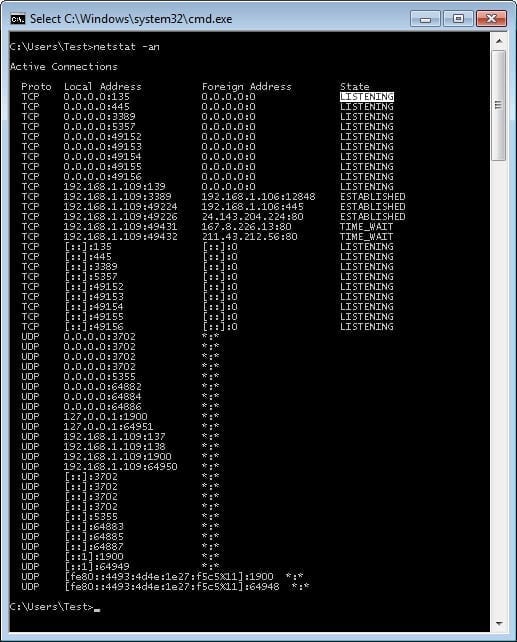
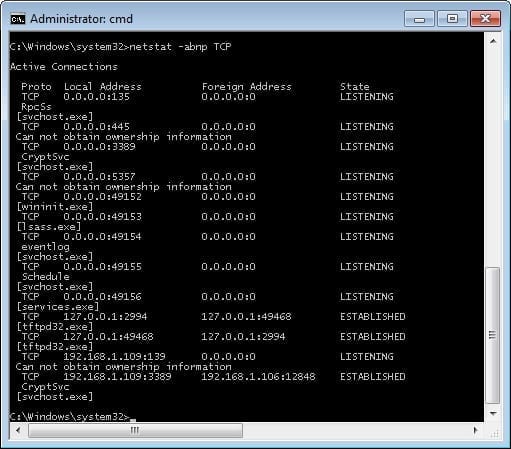
The output from the netstat command can be used to display the current state of all of the connections on the device. This is a very important part of configuration and troubleshooting. At its most basic, if a server is not seen as listening on the correct port, then no communication can occur and the troubleshooting can’t begin. The output below in Figure 3 shows that the local device is “Listening,” or waiting for an outside connection, on several ports, including TCP port 135 that I’ve highlighted in the illustration.
It should be noted that these ports may be listening but this does not mean that the firewall that is in place is actually allowing the traffic to get to the device. To remove the possibility of a host-based firewall causing a device networking problem, it can be disabled temporarily.
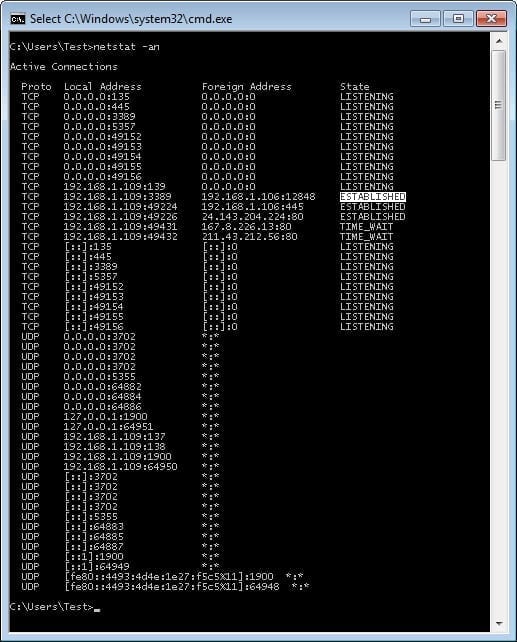
The netstat command also displays the active connections that exist on a device; this is shown highlighted in Figure 4. The specific connection that is highlighted is being used by remote desktop to capture these images.
Note that without the -a option specified, the only connections that are displayed are the active connections, shown in Figure 5.
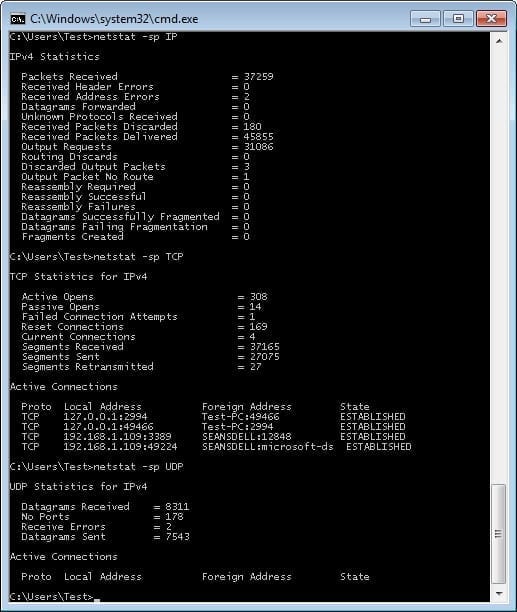
Another very important option that is available with the netstat command is the statistics option. Figure 6 shows traffic statistics for IP, TCP, and UDP.
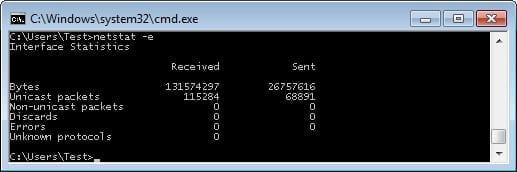
The netstat command can also be used to view the overall Ethernet statistics for a connection; this is done with the e command.
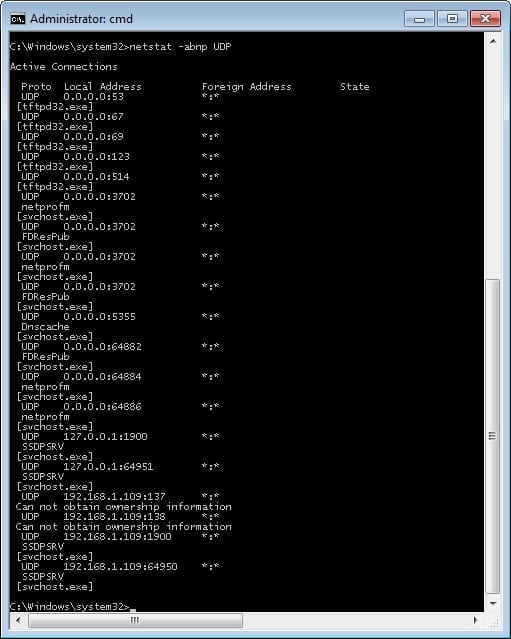
The final thing that will be covered is the often-overlooked capability of the netstat command: the ability to display the specific processes that are responsible for each individual connection on a device. This is especially important if a device is suspected of having been breached as this allows the user to display if any unauthorized processes are listening on a port. Below, figures 8 and 9 display the processes responsible for each TCP and UDP connection on the test device; the -p option is used for this purpose.
The netstat command can be a very useful tool in a number of different situations and has been supported in Windows and other platforms for a number of years. This provides for a consistent tool that is easy to learn and use. Hopefully the content in this article will introduce and/or solidify the reader’s knowledge of netstat and how it can be used to monitor your network traffic.